InsiderSecurity
InsiderSecurity Introduction
InsiderSecurity’s Automated UEBA
Why Automated UEBA?
- Uncover Internal Threats Early
Advanced security analytics that uncover suspicious user activities early, before there is any serious data loss - Advanced Sensors
Provide visibility needed to catch Advanced Persistent Threats (APTs) - Automated Threat Detection
Detect threats automatically with automated User and Entity Behavior Analytics (UEBA)
Save hundreds of hours in threat monitoring and analysis - Help to meet compliance
Align infrastructure security policy with government security standards and guidelines (e.g. EU GDPR, Singapore PDPA)
Address Key Cyber Risks Inside Your Infrastructure
- Hijacked Accounts
- Insider Threats
- Compromised Servers
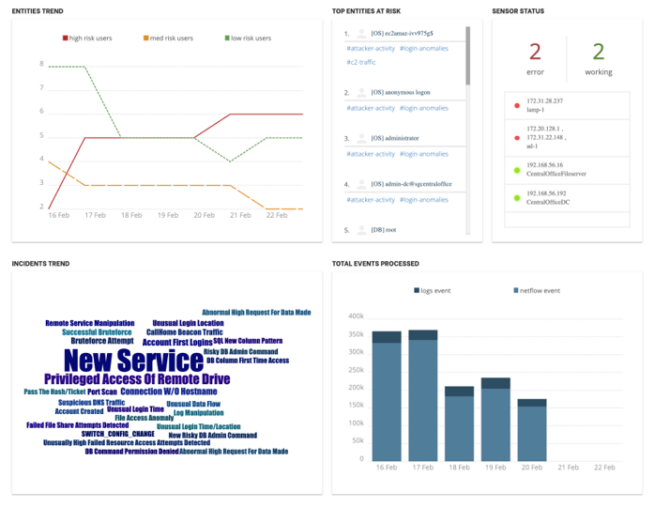
Use Cases
Compromised Privileged Account | Automated UEBA reported a suspicious privileged account. There were behaviour anomalies in the account’s activities that were similar to the actions of an attacker. Early detection enabled the customer to investigate early and prevent any serious damage. |
Data Theft by Insider Threat | Automated UEBA automatically reported a suspicious data transfer between a file repository and an employee’s machine. This was due to behavior anomalies in the file access, and unusual network traffic. The customer was able to investigate the employee and subsequently prevented a large data loss. |
Backdoor Traffic | Automated UEBA analysed network traffic for the backdoor and malware communications. |
InsiderSecurity’s Cloud Security Monitor
Why Cloud Security Monitor?
- Monitor Your Cloud Accounts And Data Activity
The solution automatically analyses the high volume of cloud events to discover compromised accounts, insider threats and suspicious data access activities early - Deploy Quickly And Work Out-Of-Box
Go live in as little as a day. Users do not need to configure complex rules. - Powerful Machine Learning
Employ the latest streaming and machine learning capabilities to identify suspicious data access and compromised accounts - Data Compliance
Help to meet data protection regulations such as PDPA and GDPR
Address Key Threats Inside Your Microsoft 365
- Rogue Administrators
- Insider Threats
- Compromised Accounts
- Data Thefts
- Suspicious Cloud Activities
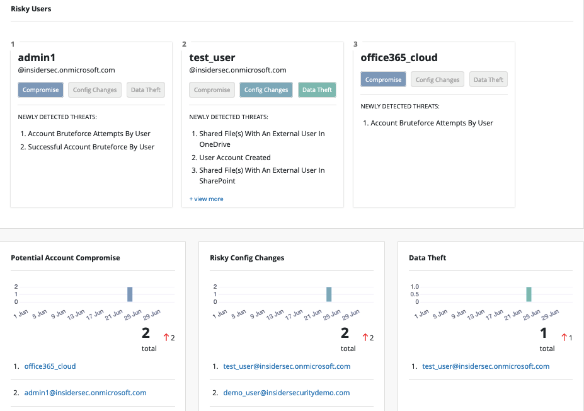
Use Cases
Data Theft | A user account had been compromised and the attacker had accessed OneDrive for Business or SharePoint Online. The attacker had gained access to sensitive or private information on OneDrive for Business or SharePoint Online and shared the sensitive information to external entities. Unauthorized shared links were constantly tracked by Cloud Security Monitor to detect suspicious access to sensitive information. |
Privilege Escalation | An unwanted user managed to obtain administrator rights, allowing him/her to perform privileged actions like removing accounts and modifying system settings. Cloud Security Monitor kept track of admin roles and access rights, and alerted when there was a high risk of privileged escalation. |
Unauthorized Policy Change | There had been a change in Microsoft Exchange Online policies to enable users to receive spam mail containing phishing or malicious content, or to forward a copy of all user emails to an attacker. Cloud Security Monitor kept track of Microsoft’s policies to detect suspicious changes in email audit settings. |
InsiderSecurity’s Database Activity Monitor
Why Database Activity Monitor?
- Automated monitor for suspicious data activity
Automatically detect suspicious database administrator activities, data theft and unusual network activities in the databases - Eliminate False Positives
Leverage machine learning, threat intelligence, and user behavior analytics to uncover complex threats with minimal noise. Reduce false positives. - Easy Deployment and Reduce Operation Cost
Monitor does not require rules to be written or maintained. Save on manpower. - Actionable Alerts
With smart algorithms making sense of events 24/7, customers get alerted only when there are high-risk activities to prevent getting swamped with alerts
What Does Database Activity Monitor Cover?
- Unusual Login Behaviour
- Risky Administrator Commands
- Suspicious SQL Commands
- Unusual Data Access
- Suspicious Failed Queries
- Malicious network traffic in the server, beyond database traffic
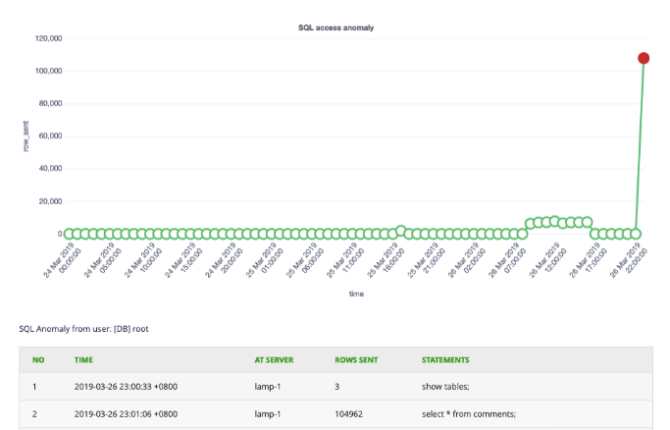
Use Cases
Insider Threat | A disgruntled employee used his/her privileged account access to steal data. InsiderSecurity detected the suspicious data access early, e.g. accessing an unusually high number of records and tables that are not normally accessed. |
Leaked Or Stolen Credentials | A hacker managed to gain access to a company network, and stole the database account credentials. When the hacker used the stolen credentials, InsiderSecurity was able to detect the suspicious login activity, abnormal account actions and data theft. |
Vulnerable Application | A vulnerability or bug in the application allowed a hacker to make unauthorised access to data stored in the database. This might be due to SQL injection or broken access control. When there was a deviation from the usual data access pattern, InsiderSecurity detected the anomaly. First-time access or permission errors in accessing the database are also detected. |
Testimonials
“InsiderSecurity has made it very easy for us to monitor our network traffic, removing the need to laboriously dig through results. It also gives us the assurance that the websites are well protected.”
– IT Director, sgCarMart
InsiderSecurity automated monitoring saves us effort and money. We don’t have to build or outsource a large IT security team. Most important of all, we get to sleep better at night.”
– Co-founder, SRX
“InsiderSecurity has cut the monitoring effort from what used to take a few hours a week to around 10 mins. This is a helpful solution.”
– Head of IT, Singapore Government Statutory Board