I was planning to write my opinions about the breach on Optus when I read about the news that Telstra was under attack as well. In case you are unaware of what has happened, in late September 2022, Optus released a statement that it was “investigating the possible unauthorised access of current and former customers’ information”. It has been further revealed that 2.1 million personal identification numbers have been stolen with 30,000 of its current and former employee details leaked as well. On early October 2022, Telstra released a similar statement and news outlets reported that 18.8 million accounts were exposed. The Telcos have maintained that they have invested in cyber security and Singtel which owns Optus is in damage control mode where it is currently assessing the potential cost of the Optus data breach.
Every organisation has its own challenges on Cyber Security. Smaller companies may not have enough budget or priority for Cyber Security, while larger organisations often have too much services to effectively manage and secure. We live in a world where services can be brought live in seconds and it is easy to forget that these services need continuous monitoring. There is also a concept of Shadow IT where users themselves subscribe or host 3rd party services simply because the IT department is not agile enough to cater to the demands of the business. I have no insights on what caused the breach beyond what was made public but based on what I have deduced, it may seem to indicate an attack related to a vulnerability exploited on external facing services.
Since no two organisations are the same, what are some of the points organisations should take note to help mitigate these threats?
In this article, I will share some of my pointers as well as notes from InsiderSecurity as we discuss five solid proven ways to prevent cyber disaster from occurring in your organisation.
1. Beware Shadow IT
Gartner refers to Shadow IT as “IT devices, software and services outside the ownership or control of IT organizations”. Training the users on the risk of Shadow IT and having the IT team be able to support the needs of the business is extremely important. Gone were the days where IT folks can ask users to wait weeks or months to get a service up because most people will simply use a search engine to find out if the service is available for them to use online. It will be a major plus point if these services are free, but in our current modern world that values data more than any other thing, are free services truly free?
2. Automate certificate services
Certificates are used everywhere, in your websites, on your email, when you use a VPN service or when your administrators log into a web portal to perform actions on hardware devices. We see a trend of maturity where larger organisations create internal Public Key Infrastructure (PKI) services to centralise control over all certificate usage. This central PKI service issues certificate for the entire organisation and provides the gateway devices the ability to block any self-signed services reducing the risk that is mentioned above. The next steps will then be the automation of not just the certificate requests via self-service but also the renewal of these certificates as well. Netrust is a well-known Singapore Certificate Authority that will be able to help on this.
3. Uncover the internal threats early
User and Entity Behaviour Analytics (UEBA) has emerged as the most effective approach to comprehensively detect a far wider range of real-time suspicious activities and unknown threats in the enterprise.
InsiderSecurity’s Automated UEBA applies algorithms, scenario analytics and advanced machine learning rather than rules or signatures to provide crucial visibility and risk score of suspicious activity. It reduces response time to cyber attacks. Based on advanced analytics of user behavior, our automated UEBA provides increased security coverage with minimal investment for security experts in SMEs.
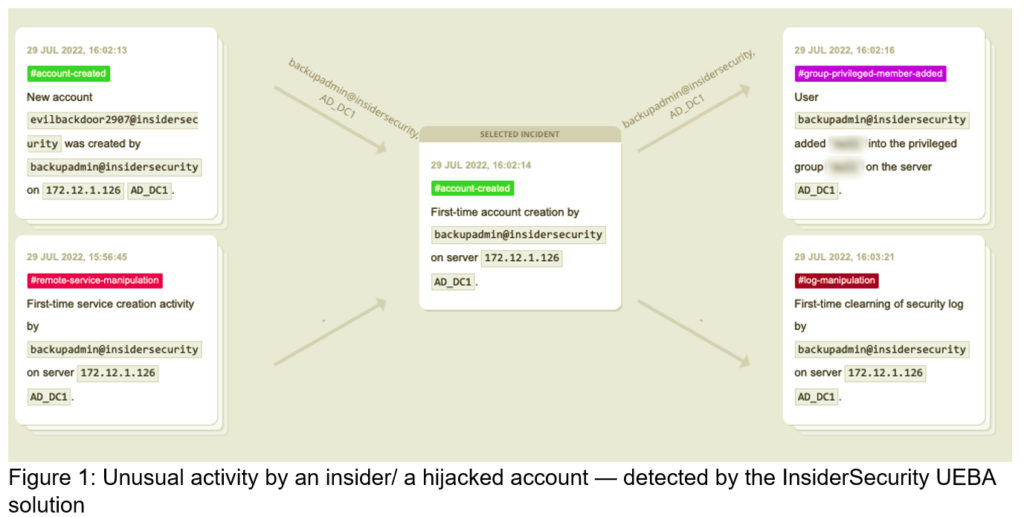
For example, consider this attack scenario. There is a zero-day vulnerability in your systems, which is not yet known to the public but is already being actively exploited by attackers. InsiderSecurity’s Automated UEBA is able to uncover such an attack by monitoring for the suspicious account and network activity in the systems and alert you early.
4. Secure the database server
Database Activity Monitor is a critical aspect of minimizing your company’s risks and protecting not only your data but also company’s reputation. For organizations with sensitive databases, InsiderSecurity’s Database Activity Monitor automatically discovers suspicious data access and data theft early. This leverages on InsiderSecurity’s AI-driven cybersecurity analytics. Database Activity Monitor works out-of-the-box as users do not need to configure complex rules. Furthermore, Database Activity Monitor helps meet data protection regulations such as PDPA and GDPR.
After attackers or rogue insiders gained initial access in a victim’s infrastructure, they will move laterally around the internal IT systems and attempt to access high-value data stored in the enterprise’s databases. InsiderSecurity’s Database Activity Monitor can discover such database access early before there is serious data loss.
5. Ensure data security in cloud services
To safeguard against the ever-evolving cloud threats, consider implementing InsiderSecurity’s Cloud Security Monitor (CSM) for managing cloud access and securing the cloud workspace. It is a simple-to-use SaaS to monitor data security in cloud services. CSM detects suspicious data access and new and emerging threats with behavioral analytics. It applies machine-built timelines to decrease response times and improve analyst productivity by automating incident investigation. CSM also monitors for compromised Microsoft 365 accounts and discovers documents shared to the public by accident.
Attackers are known to do this: after compromising an on-premise network, the attackers are able to steal the cloud credentials to access the victim’s cloud infrastructure and gain access to sensitive documents in OneDrive or SharePoint. With InsiderSecurity’s Cloud Security Monitor, such threat behaviour can be detected early to mitigate further damage.
Summary
In the past 10 years, the number of data breaches has increased significantly. Protecting the business from these threats is essential. Protect your company by using some of the approaches described above.
Clearly understanding the potential dangers from Shadow IT and the benefits of certificate automation are vital for ensuring the proper security of your organization’s critical assets. Netrust is a well-known Certificate Authority that provides such certificate services, reach out to us at sales@netrust.net or visit https://www.netrust.net/ if you would like to find out more.
It is also equally important to be able to detect the breach early. Detecting the breach early enables a company to minimize or prevent data loss altogether and avoid a cyber disaster. InsiderSecurity’s award-winning solutions help you to do this, contact hello@insidersecurity.co or visit https://insidersecurity.co/ if you would like to find out more.
Follow Netrust on LinkedIn for the latest happenings/updates.
Read more at:
